
Apart from being asource of all too frequent and embarrassing typos, Splunk is a big dataplatform which allows you to interrogate data and present results is a varietyof contexts and visualisations. I've been using it for a little over 12 months,self teaching or Googleing as I go, predominantly to sift through theterabytes of logs from various applications and appliances that get generatedin my 9-5 every day.
Cheat sheets for Splunk administration, data on-boarding, App development, search head clustering, and syslog configurations. Splunk regex cheat sheet: These regular expressions are to be used on characters alone, and the possible usage has been explained in the example section on the tabular form below. We will try to be as explanatory as possible to make you understand the usage and also the points that need to be noted with the usage. The idea is simply to save some quick notes that will make it easier for Splunk users to leverage KQL (Kusto), especially giving projects requiring both technologies (Splunk and Azure/Sentinel) or any other hybrid environments. Matches regex (2) regex: matches regex: In Splunk, regex is an operator. In Azure Monitor, it's a relational operator. Searchmatch In Splunk, searchmatch allows searching for the exact string. Random: rand rand(n) Splunk's function returns a number from zero to 2 31-1. Azure Monitor' returns a number between 0.0 and 1.0, or if a parameter. Regex command removes those results which don’t match with the specified regular expression. If we don’t specify any field with the regex command then by default the regular expression applied on the raw field. Find below the skeleton of the usage of the command “regex” in SPLUNK.

| You can use Splunk to build dashboards which are typically better than the ones that come with the product (full size) |
Cheat Sheet
I'm actively working back through my notes and adding to this all the time so it might be a good thing to reference via the URL or re-visit from time to time. I'll try to keep this as accessible as possible and base it around real world examples and use cases.
| Splunk is a great way to convert reams of log data into views which mean something (full size) |
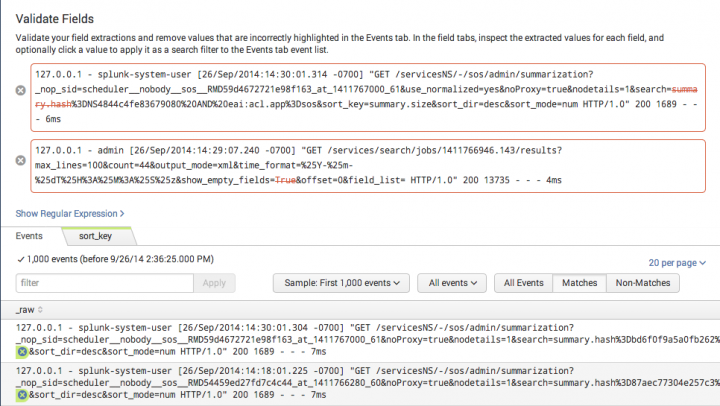
Of course, there is a wealth of documentation over at http://docs.splunk.com and I'd highly recommend that if you start using Splunk you start there or at least turn to that as your primary reference. I'd also strongly recommend that you check to see if there is an existing Splunk App if you have a very specific requirement. Why re-invent the wheel if the vendor (or the community) has already built an app for that appliance / application you've just installed?
| Like maps? No problem (full size) |
I intend to write a separate piece about some of the very clever things you can do with Splunk, especially some of the instances where we currently use it as the center for an automation piece. It's not just reports and dashboards that Splunk can power - with a bit of thinking and tinkering you can get it to interact and respond to your environment, making it a very powerful tool to add to your security arsenal. I'll still add any searches and code for these solutions to the cheat sheet but I want to expand on them sufficiently so people can follow the recipe to bake their own.
Eval And Regex Splunk
